The Outsourcing Compliance Playbook: Rules They Don’t Teach You
Offshore software? Here’s what every founder and CTO needs to know about staying compliant without growing gray hair.

From IP handoffs to country-specific gotchas - your legal radar needs more than NDAs and wishful thinking
Let’s start with a confession: early on at 1985, we thought “compliance” just meant slapping an NDA on every doc, asking devs to use strong passwords, and hoping no one stored production keys in Google Sheets. (Spoiler: they did.)
Turns out, the real game is way messier. And when you’re outsourcing engineering work across borders - especially with IP-heavy projects - the unspoken rules matter more than the ones your lawyer cuts and pastes from that 2016 SaaS contract.
This isn’t a legal lecture. It’s a practical survival guide from someone who’s waded through GDPR audits, dealt with Indian labor inspectors, negotiated IP clauses with five different jurisdictions, and once explained to a founder why their “friend in Eastern Europe” didn’t actually transfer IP rights.
If you’re shipping serious product with offshore help, here’s what you really need to know.
Rule #1: IP Doesn’t Transfer Itself (Even If You Paid for It)
Let’s kill the most common myth first: “If I paid them to build it, I own it.”
Nope.
Payment ≠ ownership, at least not automatically. In many jurisdictions - including India, the Philippines, and a good chunk of Europe - you need explicit, written assignment of intellectual property. Not just in the master agreement, but ideally in every statement of work (SOW) and subcontractor agreement too.
I’ve seen startups raise their Series A only to discover that their entire codebase was legally co-owned by a freelance team they’d ghosted. Investors don’t love that.
Checklist:
- Include an “Assignment of Work Product” clause in every agreement.
- Ask your offshore partner to ensure their employees and contractors sign “back-to-back” IP assignments.
- In the US? Consider a “work made for hire” clause. Outside the US? Don’t assume it applies.
Pop-culture reference break: This is the legal version of The Office’s “I declare bankruptcy!” scene. Just saying the thing doesn’t make it true.

Rule #2: Don’t Copy-Paste That NDA
A good NDA is like a prenup - it won’t stop the bad stuff from happening, but it helps clean up the mess.
A bad NDA? Might as well be a blank Google Doc.
Most companies grab a boilerplate NDA and call it a day. But offshore work involves:
- Multiple jurisdictions
- Varied definitions of “confidential”
- Subcontractors you’ll never meet
Your NDA needs to account for all of this.
What we learned the hard way:
One of our early clients had a Chinese firmware vendor sign a US-style NDA. It didn’t include provisions enforceable under Chinese law. Two years later, a copycat product showed up at a Shenzhen trade show. Oops.
Better move:
Customize your NDA for jurisdictional enforceability, and make sure it survives termination (you’d be surprised how many don’t).
Rule #3: GDPR, HIPAA, ISO, SOC2 - Don’t Play Compliance Bingo
Slapping every acronym into your RFP doesn’t make you safer. It just confuses everyone.
Instead, map your compliance needs to:
- Where your users are (Data protection: GDPR, CCPA, etc.)
- What industry you’re in (Healthcare = HIPAA; Fintech = PCI-DSS)
- Who your customers are (Enterprise clients often require SOC2/ISO27001)
True story: A fintech prospect once asked if we were “GDPR certified.” That’s not a thing. You can comply with GDPR, but there’s no certification.
If you’re using offshore devs for regulated data:
- Ensure contracts clearly define who is the Data Controller and who is the Data Processor.
- Ask where code is stored, where data flows, and who has access.
- Use role-based access controls. Shared AWS credentials? Welcome to audit hell.

Rule #4: Country Laws > Contract Clauses (Sorry, Delaware)
Say your MSA says Indian developers will follow US IP law. That’s adorable.
But if your developers are employed by an Indian company - or even freelancers with residency - Indian labor and IP law still applies. Your contract can’t override that.
What you can do:
- Choose arbitration venues that make enforcement easier (Singapore and London are popular for cross-border deals).
- Use “choice of law” provisions that give you predictability.
- Work with partners who actually understand their own country’s compliance obligations.
Bonus gotcha: Some countries have mandatory severance rules or limits on fixed-term contracts. If you’re treating contractors like full-timers, be careful.
This is the “Jurassic Park logic” of compliance: just because you can draft the clause doesn’t mean nature - aka foreign law - will let it live.

Rule #5: Shadow Teams = Shadow Risk
That 5-person team you hired? Might actually be 12.
Offshore vendors sometimes subcontract, silently. This isn’t always bad - but if those subcontractors haven’t signed the same IP and confidentiality agreements, your legal protection is full of holes.
Worse, you won’t know until something goes sideways. Like when an engineer you’ve never met starts posting bits of your dashboard on GitHub.
What we do at 1985:
- Every dev signs a customized invention assignment agreement before their first commit.
- We share contributor logs during client handoffs.
- We audit third-party tool access quarterly.
You don’t need to micromanage. But you do need transparency.
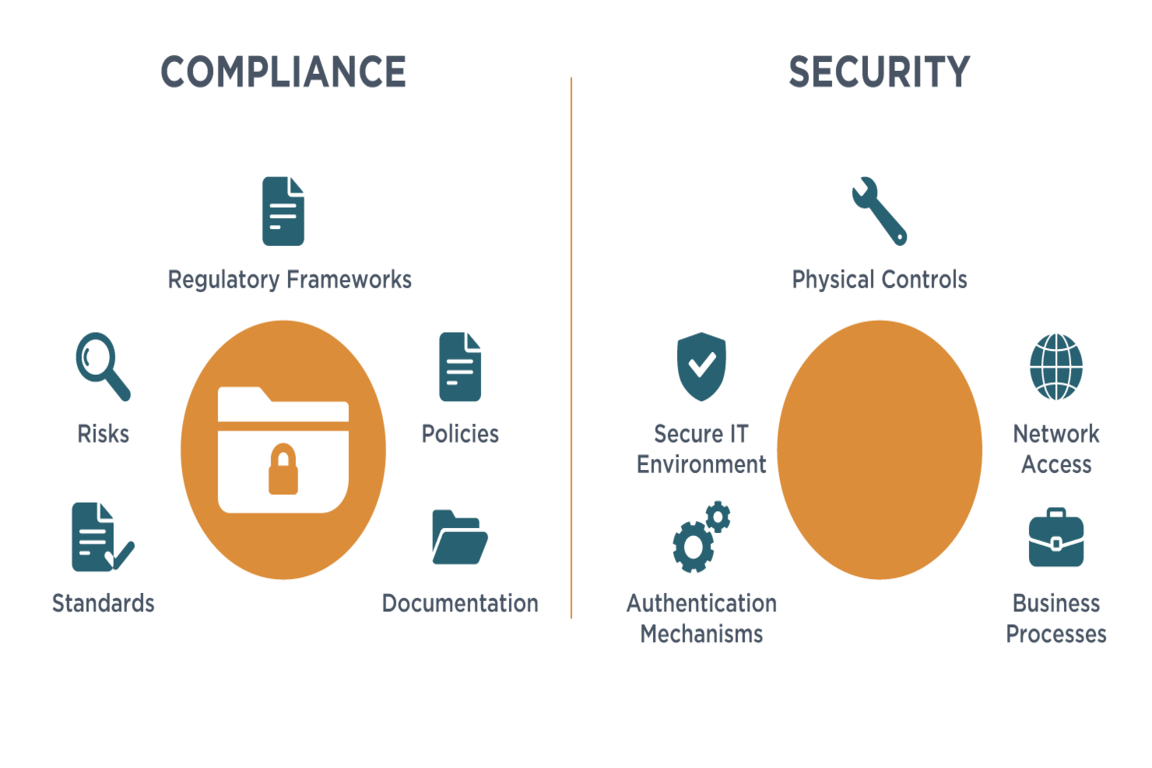
Rule #6: Compliance ≠ Security ≠ Privacy
People conflate these constantly. They’re cousins - not twins.
- Security is about protecting systems from bad actors.
- Privacy is about user rights and data usage transparency.
- Compliance is about meeting external requirements.
You can be secure but non-compliant. You can be compliant but leak data (hello, Facebook fines).
If your dev team handles PII or customer data:
- Check their data retention and deletion practices.
- Confirm where backups live.
- Ask if their employees access client data from personal laptops or shared machines.
We once had to walk a client through hardening a Ukrainian dev laptop fleet after we discovered they were downloading prod dumps for debugging. Not malicious - just unaware.
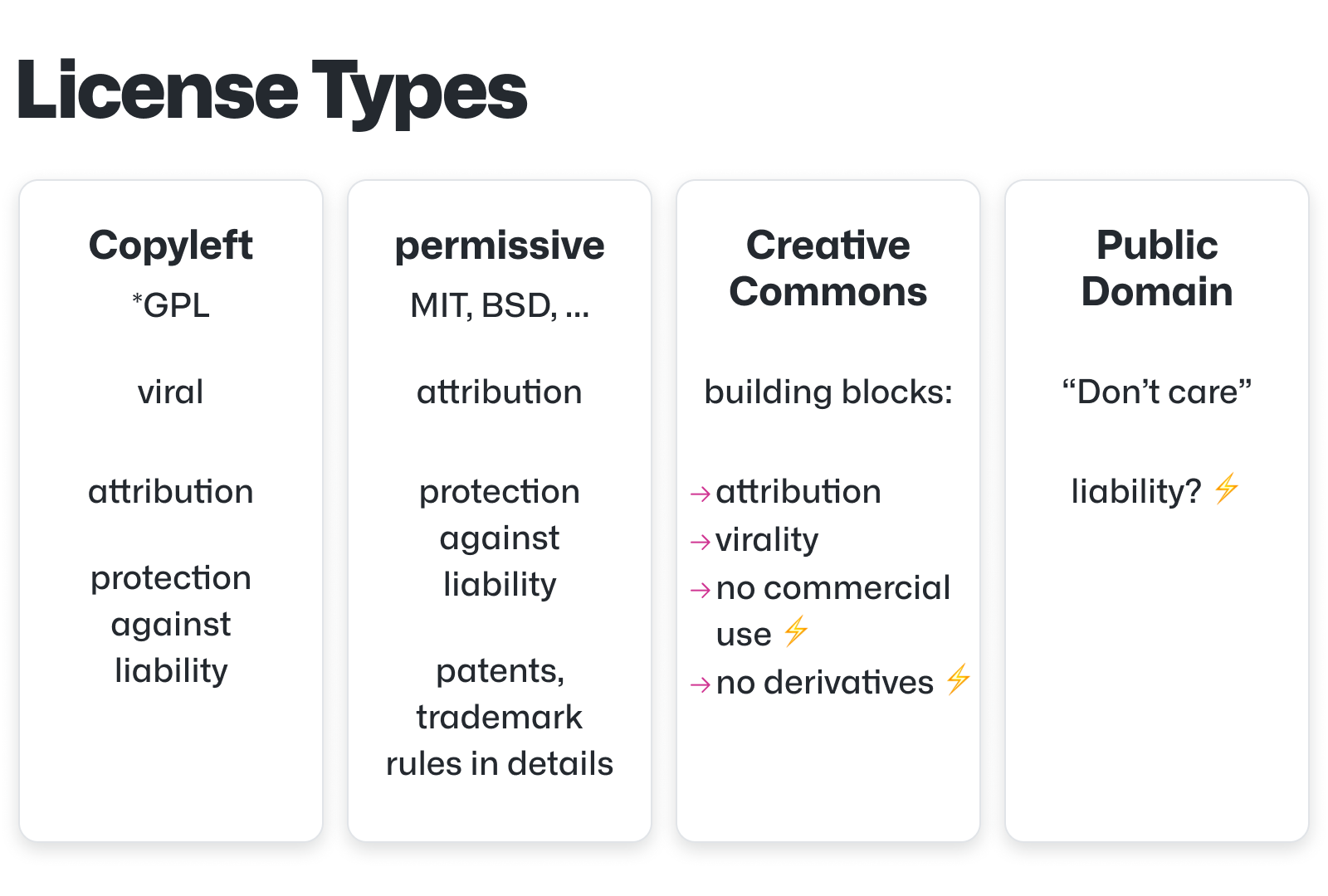
Rule #7: Don’t Let Devs Use “Free” Stuff Blindly
You might trust your offshore team with your codebase. But can you trust them with open-source licensing?
If your devs add GPL-licensed code to your proprietary repo, congratulations - you just created a licensing bomb.
At 1985, we do:
- Automated license scanning during CI.
- Clear guidelines on what OSS licenses are allowed.
- Training for new engineers on open-source dos and don’ts.
No one wants to explain to a potential acquirer why a key feature technically belongs to the public domain.
Common Pitfalls and How to Dodge Them
Q: Can’t I just use a dev shop that “promises” they handle compliance?
Only if you’re ready to trust verbal assurances over documented processes. Ask for their policies. Ask how they vet subcontractors. Ask for a sample contract.
Q: What if my vendor uses GitHub Copilot?
Good question. You need to understand what code suggestions are allowed, whether they store your prompts, and what rights you retain over generated code.
Q: Is storing data in the cloud enough to be compliant?
Nope. Where the cloud lives (region), who can access it, and how you control it matters more. AWS in Singapore ≠ AWS in Frankfurt.
Q: Do I need to do compliance audits?
If you’re in a regulated space or working with enterprise customers - yes. Even lightweight internal audits can prevent future legal drama.
Wrap-up
Outsourcing can absolutely accelerate product delivery - but not if you treat compliance as an afterthought. It’s the scaffolding that protects your product, your users, and your valuation when the stakes rise.
You don’t need a battalion of lawyers. You need:
- Clear contracts
- Good hygiene
- A partner who gives a damn
Because in this game, the rules aren’t always written. But the consequences sure are.
Want to build smarter, safer, and sleep-better-at-night-er? Hit me up. The 1985 crew has seen the compliance monsters under the bed - and we know which ones actually bite.
FAQ
1. Do I automatically own the IP if I pay an offshore developer or agency to build my product?
No, not by default. In many jurisdictions, intellectual property rights do not automatically transfer with payment. You must include explicit IP assignment clauses in your contracts - and ideally in individual statements of work. Ensure your vendor also has "back-to-back" IP agreements with their employees or contractors to fully protect your ownership.
2. What should I look for in an NDA when outsourcing across borders?
Beyond standard confidentiality clauses, make sure the NDA includes enforceability provisions specific to the developer’s jurisdiction. Confirm that confidentiality obligations survive termination, and account for subcontractor access. The NDA should clearly define what constitutes confidential information and how it must be handled and destroyed post-project.
3. What’s the difference between security, privacy, and compliance in offshore development?
Security protects systems from threats. Privacy governs how user data is collected, used, and disclosed. Compliance refers to meeting legal or industry requirements like GDPR, HIPAA, or SOC 2. Being compliant doesn't guarantee strong security, and having great security doesn’t mean you’re legally in the clear on privacy.
4. If my code is stored in the cloud, is that enough to be compliant with data regulations?
No. The geographic location of the cloud server matters, especially for regulations like GDPR or CCPA. You must also control access, encrypt sensitive data, log who accesses what, and establish clear data retention and deletion policies. Simply using AWS or Azure doesn’t equal compliance.
5. How do I make sure open-source code used by offshore teams won’t create licensing issues?
Use automated license scanners in your CI pipeline, and create a whitelist of acceptable OSS licenses. Educate your teams - internal and external - on which licenses (e.g. MIT, Apache 2.0) are safe for commercial use, and which (e.g. GPL, AGPL) may require you to open-source your own code in return.
6. Can I just rely on my offshore vendor’s word that “compliance is handled”?
No. Ask for their actual compliance documentation, including data access policies, employee onboarding checklists, and subcontractor agreements. Ensure they provide a list of who will have access to your IP and data. Treat verbal assurances as red flags unless they’re backed by written processes.
7. What clauses should I include in my contract to protect my IP internationally?
You should include: an Assignment of Work Product clause, a clause covering subcontractors and affiliates, a confidentiality clause that survives termination, and a governing law and dispute resolution section. Also, consider including warranties on IP originality and indemnity against infringement claims.
8. How can I check if my offshore vendor is GDPR or HIPAA compliant?
Request documentation of their data protection practices: privacy policies, breach notification workflows, encryption standards, and employee training records. For HIPAA, ask about Business Associate Agreements (BAAs). For GDPR, confirm they understand their role as a Data Processor and have appointed a Data Protection Officer (if required).
9. What’s the risk of subcontractors I don’t know about working on my product?
High. If subcontractors haven’t signed the same IP and confidentiality agreements, your legal protection is diluted. You may lose clear IP ownership or risk data leaks. Demand transparency about the full team, their roles, and their contractual obligations to mirror your master agreement.
10. What are common compliance mistakes companies make with offshore teams?
Common missteps include: assuming payment equals IP transfer, failing to assign rights down the contractor chain, ignoring jurisdictional legal conflicts, underestimating open-source license risks, storing regulated data in non-compliant regions, and conflating security with full compliance. All of these can create legal liabilities down the line.



