Your Health App Shipped. Is It Compliant, or Just Lucky?
Shipping a health app? Don't let hidden compliance traps sink your startup. We break down the real risks (HIPAA, FDA, & more) and how to avoid them.

Why ticking “yes” on a privacy prompt doesn’t mean you’re HIPAA-safe - or lawsuit-proof

If you’ve built a health tech product - an AI-powered symptom checker, a fitness+mental health tracker, or a SaaS backend for clinics - you’ve probably shipped first and googled HIPAA later. And I get it. Product velocity feels more urgent than privacy compliance. Until it doesn’t. Like when Apple boots your app for data mishandling. Or when you realise your Firebase logs casually exposed PHI (Protected Health Information). Or worse, when a privacy audit makes you sound like you engineered in a garage using duct tape and divine grace.
“But We're Just a Wellness App!”
That’s the defence I hear most. You don’t store patient records. You’re not a hospital. You’re helping users meditate, hydrate, or manage migraines. Surely that doesn’t make you a “covered entity,” right?
Well, here’s the catch: HIPAA compliance isn’t about what you think your app is. It’s about how you handle data and who you're handling it for.
Let me break it down like we did for a mental wellness startup in Bangalore: They didn’t think they were covered under HIPAA because they didn’t operate in the U.S. But their B2B customers did. One of them was a U.S.-based employer offering wellness perks to employees. Boom - business associate. Suddenly that tiny checkbox in the onboarding form wasn’t enough to keep the regulators at bay.
And no, saying "we don't store data, we just process it" won't save you. HIPAA is like Mumbai traffic cops - you may not see them, but you don't want to be caught in the wrong lane when they show up.

The Compliance Mirage: When Devs Think Infra = Safety
Let’s talk infrastructure.AWS has a BAA? Great. Firebase says they’re HIPAA-ready? Nice. You've encrypted your S3 buckets? Beautiful. But unless your entire application logic treats PHI with the paranoia of a hacker at DEF CON, you're playing compliance Jenga.
Here’s how this plays out in the wild:
- A well-meaning dev logs user error messages that accidentally include names and symptoms. Whoops - PHI just got stored in plain text.
- A dev uses Mixpanel or Google Analytics without scrubbing IDs. Congrats, you just sent sensitive health data to an analytics vendor who doesn't have a BAA with you.
- Someone enables crash reporting with full memory dumps. Guess what’s in that memory? Yup. More PHI.
We’ve done security audits where the infra looked airtight - but app logs, webhook payloads, and third-party tools were leaking like a sieve. Compliance isn’t just a checklist. It’s a culture of defensive design.
The Great BAA Misunderstanding
Ah, the Business Associate Agreement. The piece of paper that startups think turns their AWS deployment into Fort Knox. I’ve seen founders treat BAAs like infinity stones - just collect all of them and you’re invincible.
Not quite.

A BAA is a requirement, not a shield. It ensures your vendor agrees to handle PHI responsibly. But here’s the kicker: it’s only valid if you use their services correctly. Misconfigure a logging tool, forget to restrict access, or mislabel a database - and no BAA in the world will save you from OCR (Office for Civil Rights) scrutiny.
Fun fact: in 2023, a small U.S. telehealth startup got hit with a $275K fine after signing BAAs - because their app logic still allowed PHI to be sent to non-compliant partners. That’s like locking your front door and leaving the windows wide open.
What We Got Wrong (And Fixed, Fast)
We’ve face-planted on this ourselves. One of our early clients, a remote physiotherapy SaaS, had a patient calendar module we helped build. We were so focused on feature velocity that we didn’t realise Google Calendar API was being used in a way that exposed patient names in unprotected calendar invites.
We caught it during a pre-launch review. Rebuilt the sync logic using pseudonymised IDs and encrypted metadata. But it was a sweaty weekend.
Lesson? Don’t assume your integration is HIPAA-safe just because it’s shiny and from Google. Always check how data flows and where it ends up.
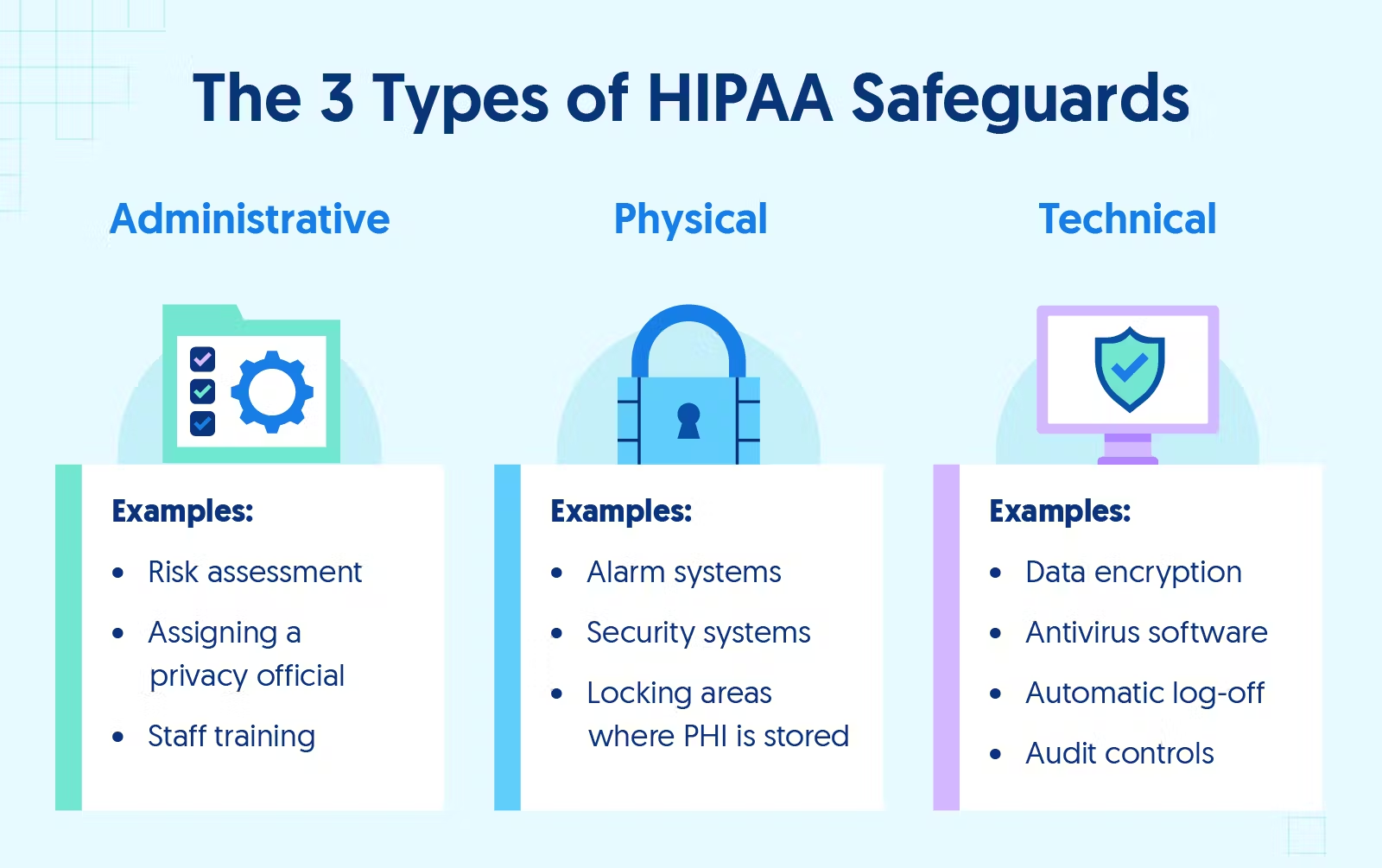
7-Step Checklist That’s Actually Worth Following
Most compliance guides feel like they were written by corporate lawyers who haven’t shipped code since Netscape was cool. So here’s our no-BS playbook for building HIPAA-smart apps:
- Know if you’re a covered entity or a business associateIf your customers are providers, insurers, or employer wellness programmes - you're likely a business associate. That means HIPAA rules apply, even if you don't store records directly.
- Minimise PHI exposure by defaultDon’t collect names, DOBs, or medical info unless you absolutely need them. Can you design your app to work anonymously? Do it.
- Designate a HIPAA Privacy Officer - even if it’s just you in a hoodieSomeone needs to own this. Track what counts as PHI, who can access it, and how it’s secured. Yes, Notion is fine for documentation (until you scale).
- Use vendors who’ll sign BAAs - and configure them correctlyAWS, GCP, Twilio, SendGrid all offer HIPAA-compliant setups. But only if you follow their docs to the letter. Skim the docs = shoot yourself in the foot.
- Log responsiblyScrub PHI from logs, limit retention, restrict access. Set alerts for when someone turns on verbose logging in prod (ask me why).
- Encrypt everything, not just storageData in transit, backups, logs, internal APIs - all need end-to-end encryption. Use TLS 1.2+ and rotate keys like you rotate cricket captains.
- Do a mock audit before an actual oneWalk through your app like you're an auditor. Where does PHI enter? Where does it go? Who touches it? Spoiler: You’ll find at least one oopsie.
Reality Check: It’s Not Just HIPAA Anymore
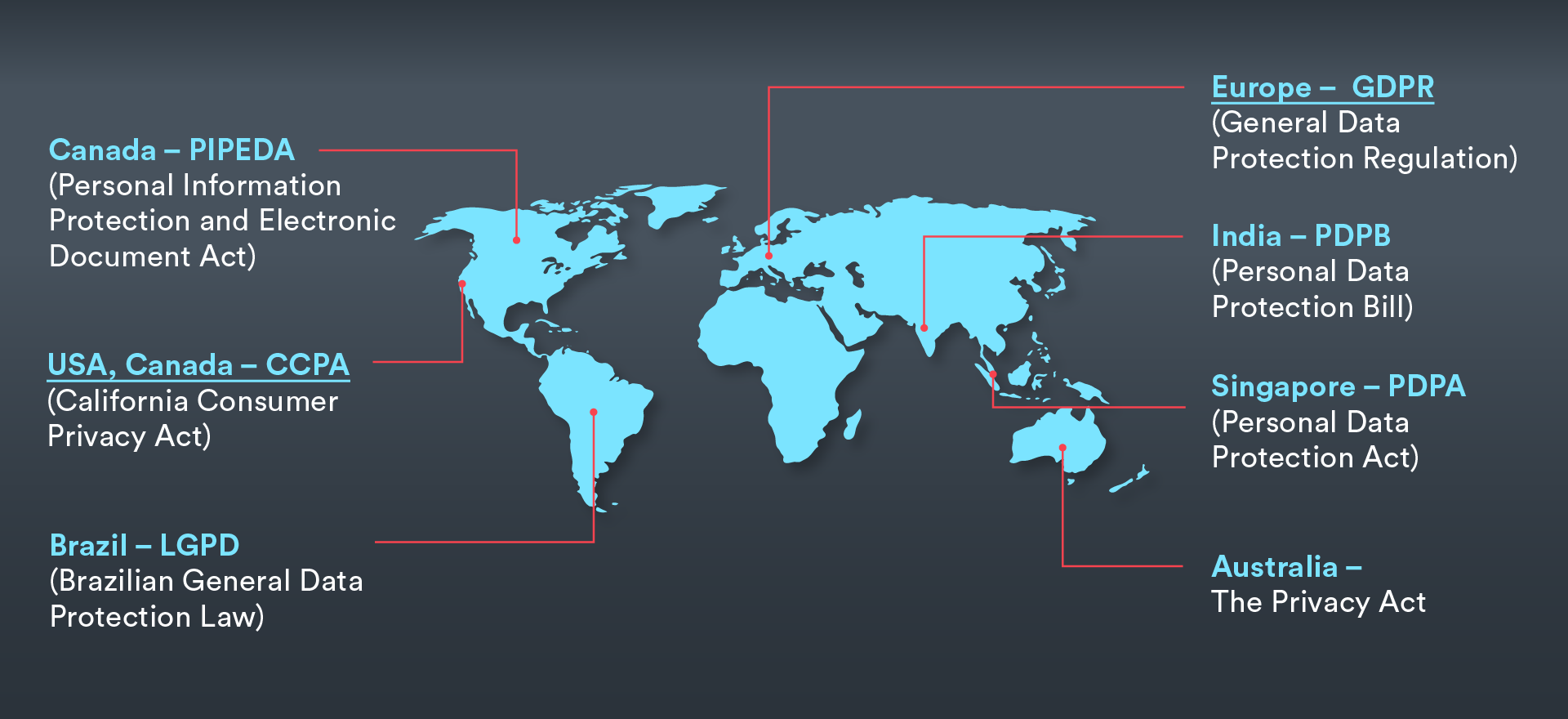
HIPAA is the poster child, but compliance isn’t a U.S.-only problem. The moment you deal with international users or enterprise clients, you’re juggling:
- GDPR (EU): Broad definition of personal data. Consent isn’t optional fluff.
- PIPEDA (Canada): Covers consent, access, and correction rights.
- DPDP (India): New kid on the block. Covers digital personal data and obligations for data fiduciaries.
- State-level laws (California, Illinois, etc.): HIPAA ≠ CCPA. Learn the alphabet soup.
If you’re building healthtech in 2025, you're not just shipping software - you’re signing up to run a miniature compliance programme. Don't wait till an angry parent DMs you on LinkedIn about a breach.
Ship/Skip Scorecard
If it smells like PII, treat it like PHI. Better to overdo it than under-think it.
Wrap-up
Building a health app isn’t just about user delight and retention. It’s about building trust at a technical level. Because no one remembers your sleek UI if their data lands in the wrong hands. The good news? Compliance isn't rocket science - it’s just software with grown-up guardrails.
Want devs who get both privacy and product velocity? Let’s talk. Our Bangalore crew won’t let PHI sneak past the firewall.
FAQ
1. If my app doesn’t store medical records, do I still need to worry about HIPAA?
Yes. HIPAA isn’t just about storage—it’s about access, transmission, and usage of protected health information (PHI). If your app collects or even temporarily processes health-related data on behalf of a covered entity (like a clinic or insurer), you’re in scope. “We don’t store it” is not a valid escape hatch.
2. What counts as PHI (Protected Health Information)?
PHI includes any health data tied to a personally identifiable marker—think names, emails, birthdates, symptom logs, device IDs, or even timestamps if they can be linked to a user’s health status. It’s a wider net than most devs assume. Better to assume it’s PHI and design defensively.
3. I use Firebase. Isn’t that HIPAA-compliant already?
Firebase can be configured for HIPAA compliance if you use only specific services under a signed BAA with Google. Many Firebase tools—like Analytics or Crashlytics—are not HIPAA-eligible. Just using Firebase doesn’t make you compliant. You need to tailor your stack and use it with surgical precision.
4. Do I need to sign BAAs with every vendor in my stack?
If a third-party service has access to PHI—whether via logs, storage, or processing—you must have a signed Business Associate Agreement (BAA) with them. This includes cloud hosting, comms APIs, backups, even some dev tools. If a vendor won’t sign a BAA, you can’t use them with PHI, full stop.
5. Can I use analytics tools like Mixpanel or Google Analytics in a HIPAA-compliant health app?
Usually no. These tools often collect device IDs, IP addresses, and behavioural data that—when combined with health info—count as PHI. Unless they explicitly support HIPAA and sign a BAA with you (most don’t), you’re better off using self-hosted or privacy-first alternatives that give you tighter control.
6. We’re not in the U.S.—does HIPAA still apply to us?
If your users, partners, or customers are in the U.S. healthcare ecosystem (including employers offering wellness benefits), then yes, HIPAA can still apply. Geographic location doesn’t exempt you if your app interacts with U.S.-based PHI. HIPAA follows the data, not just the dev team.
7. Is encrypting everything enough to be HIPAA-compliant?
Encryption is essential, but it’s just one piece. You also need access controls, audit trails, breach procedures, minimum data collection practices, and proper vendor agreements. Think of encryption as the seatbelt—it helps, but you still need working brakes, mirrors, and a driver's licence.
8. How do I avoid accidentally logging PHI in my backend systems?
Scrub logs aggressively. Set up logging middleware to redact or mask sensitive fields, restrict log levels in production, and monitor for log bloat from error messages or crash reports. Be extra cautious with verbose logging, especially from mobile SDKs or unfiltered API payloads.
9. What’s the easiest way to check if I’m leaking PHI without realising it?
Do a manual or automated audit of data flows. Map every input (forms, APIs, integrations) and trace where that data goes—logs, databases, third parties, or UI debug tools. You’ll often find PHI in places you didn’t mean to put it. Bonus tip: turn on verbose logging in staging and inspect payloads with fresh eyes.
10. How often should I audit my app for compliance issues?
Quarterly is a good baseline, but it should also be part of every major release cycle, especially if you’re shipping new data flows, integrations, or analytics tools. Build a culture where compliance is baked into your QA—not tacked on after launch.



