Your Hybrid Cloud Isn't Hybrid (Yet): A Leader's Fix
Is your hybrid cloud just adding complexity? Learn how tech leaders build manageable strategies that deliver results.

Is your hybrid cloud strategy just lipstick on a legacy pig? Many are. They promise flexibility but deliver complexity. They chase cost savings but find spiraling egress fees. The truth? A staggering 66% of organizations cite optimizing existing cloud spend as their top initiative, suggesting many hybrid setups aren't hitting the mark. It’s not about if hybrid, but how. Get it wrong, and you’re building technical debt on two fronts. Get it right? You unlock genuine agility. This isn't theory. This is the roadmap forged in the trenches with companies like yours.
Let's cut the fluff. You need a plan that works.
The Illusion of Seamless Integration
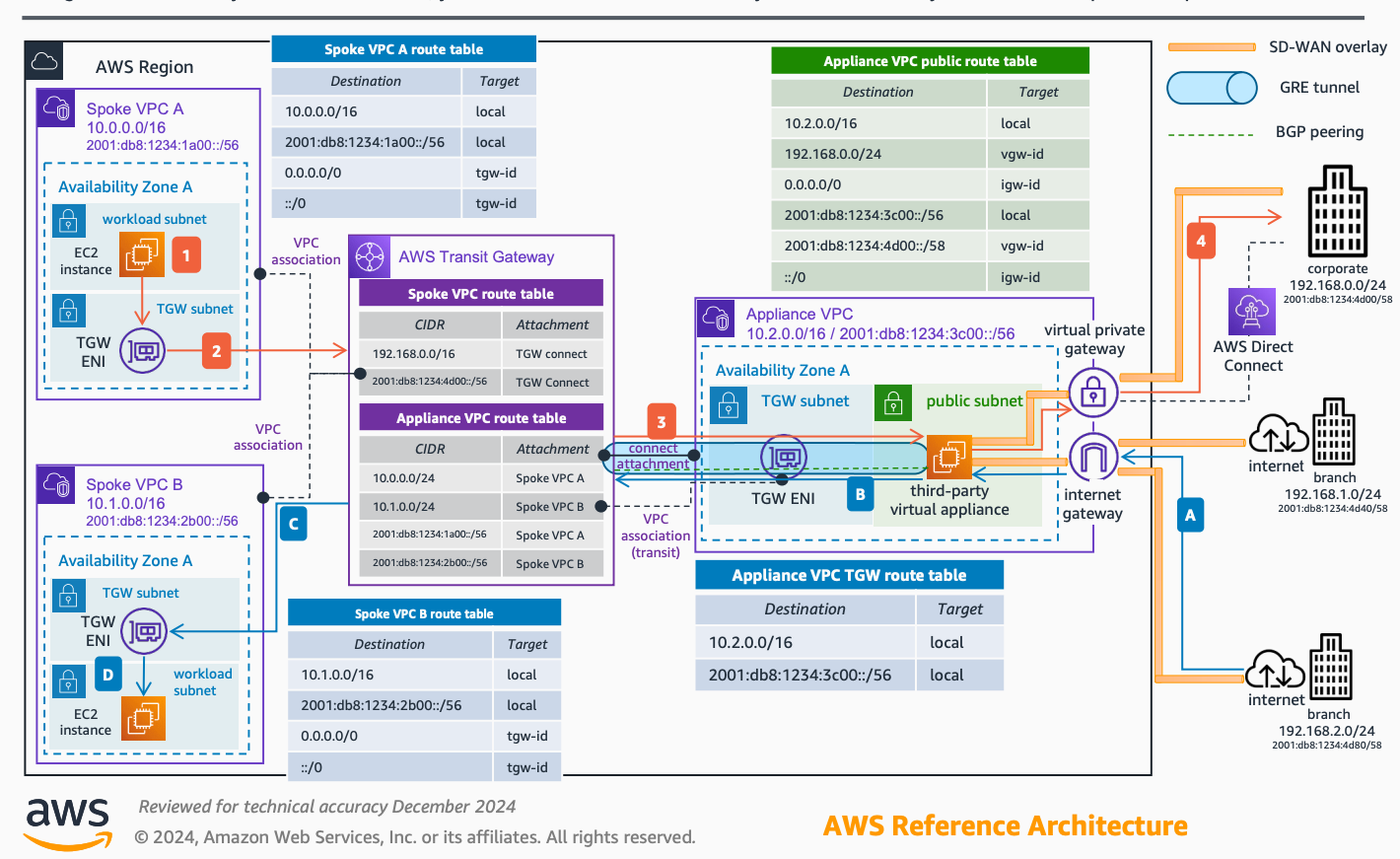
Hybrid cloud isn't plug-and-play. It demands deliberate architecture. Too many teams treat public and private clouds as separate kingdoms. They bolt them together with brittle scripts and manual processes. Disaster waits. The goal isn't just connecting resources; it's unified orchestration. It’s consistent management. It’s workload portability that actually works. Forget the marketing hype. Focus on the plumbing.
Data and Dependencies
Where does your data live? Where should it live? Data gravity is real. Moving large datasets incurs cost and latency. Ignoring application dependencies leads to performance nightmares. You can't just sprinkle workloads across clouds.

The Data Dilemma: A common pitfall we see at 1985 involves underestimating data transfer costs. One e-commerce client planned to run analytics bursts in the public cloud against their on-premise transactional database. The egress charges nearly crippled their budget within a quarter. They assumed "hybrid" meant "free flow." It doesn't. According to [Gartner research trends (pre-2025 knowledge)], data gravity and integration complexities remain significant barriers to multi-cloud adoption strategies, impacting cost and performance. Understand your data flows before you architect. Map them obsessively.

Dependency Mapping Nightmare: Another client, a SaaS provider, tried a phased migration. They moved front-end services to the public cloud while keeping backend monoliths on-prem. Latency between tiers killed user experience. Why? They hadn't mapped the chatty, synchronous calls between services. The fix required significant re-architecting, delaying their roadmap by six months. Internal 1985 audits consistently find incomplete dependency mapping in over 70% of initial hybrid assessments. Don't guess. Profile your applications.

Before migrating anything, establish strict performance baselines for communication between your intended private and public cloud segments. Simulate realistic traffic. If baseline latency exceeds application tolerances, rethink your workload placement now, not after deployment.
Security: The Fractured Perimeter
Your attack surface just doubled. At least. Managing security consistently across disparate environments is non-trivial. Different tools, different APIs, different skill sets required. Patchwork security is no security.
Inconsistent Policies: We often inherit environments where security policies applied on-premise are manually (and often incorrectly) translated for the cloud. A financial services client discovered their public cloud object storage buckets were inadvertently left public-facing due to a misconfigured Infrastructure-as-Code (IaC) template. This basic error stemmed from teams working in silos. Unified security posture management isn't optional. It’s table stakes. Breaches often exploit these inconsistencies.
Identity Sprawl: Managing identities and access across hybrid environments? Chaos, usually. Separate directories, duplicated roles, inconsistent permission models. A healthcare tech company we worked with faced compliance issues because access controls weren't synchronized. An employee who left the company still had active credentials in their public cloud environment for weeks. Centralized Identity and Access Management (IAM) that spans all environments is critical. As one CISO told us anonymously, "Hybrid cloud doubled my identity headaches overnight."
Mandate the use of security tools and platforms that explicitly support hybrid environments from day one. Can your vulnerability scanner see both sides? Does your SIEM ingest logs uniformly? Is your IAM truly centralized? If not, you have critical gaps.
Building the Bridge: Orchestration and Containers
This is where the rubber meets the road. How do you deploy, manage, and scale applications consistently, regardless of where they run? Manual processes won't cut it. You need automation. You need standardization. Enter containers and orchestration.

Kubernetes: The De Facto Standard (With Caveats)
Kubernetes (K8s) promises workload portability. Run your containers anywhere K8s runs. It's powerful. It's complex. It's not a silver bullet.
The Complexity Tax: K8s is powerful, but managing it across hybrid environments requires significant expertise. CNCF surveys (pre-2025 data) consistently show a shortage of skilled Kubernetes professionals. We’ve seen teams adopt K8s enthusiastically, only to drown in the operational overhead of managing clusters, networking (like CNI choices), and storage (CSI drivers) across different infrastructures. One client spent more engineering effort managing their hybrid K8s platform than building product features for nearly a year. Don't underestimate the learning curve and operational cost.
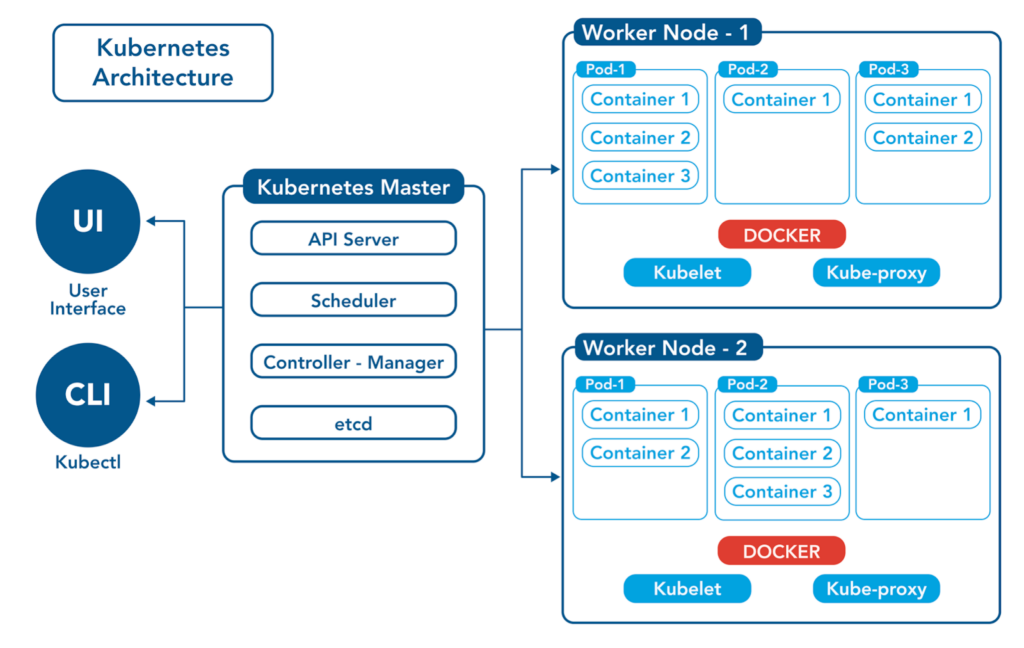
Vendor Lock-in (Disguised): Managed Kubernetes services (EKS, AKS, GKE, OpenShift) ease the burden. But beware subtle lock-in. Features, networking integrations, and IAM often tie you closer to a specific cloud provider, even if the core K8s API is standard. A media company using a managed K8s service found migrating stateful applications to their private K8s cluster challenging due to dependencies on cloud-specific storage provisioners. True portability requires discipline in avoiding proprietary extensions.
Be honest. Do you really need to move any workload anywhere instantly? Or do you need consistency for specific application tiers? Tailor your K8s strategy (managed vs. self-hosted, choice of ingress/service mesh) to your actual portability requirements, not a theoretical ideal. Start simple.

Beyond Kubernetes: Serverless and PaaS
Not every workload needs K8s. Serverless functions (Lambda, Azure Functions, Cloud Functions) and Platform-as-a-Service (PaaS) offerings can simplify deployment for specific use cases, even in a hybrid model (e.g., using Knative or OpenFaaS on-prem).
The Right Tool for the Job: A retail client initially planned to containerize everything. We helped them identify event-driven processing tasks (like image resizing on upload) perfectly suited for serverless functions deployed in the public cloud, triggered by events from their on-prem systems. This reduced operational overhead and cost compared to running persistent K8s pods for these bursty tasks. Over-reliance on a single orchestration model is inefficient.
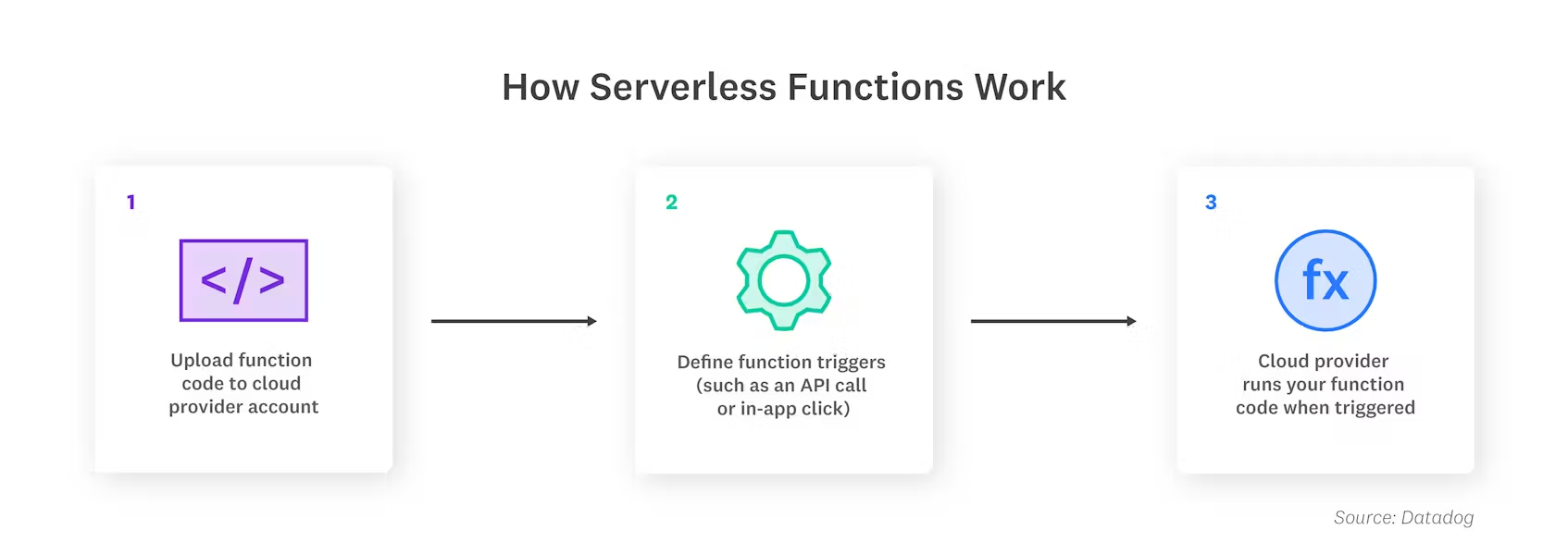
Hybrid PaaS Challenges: Integrating on-premise PaaS (like Cloud Foundry, or Knative on K8s) with public cloud PaaS requires careful consideration of feature parity, networking, and developer experience. We've seen friction where developers face different deployment mechanisms and monitoring tools depending on the target environment. Aim for a consistent developer workflow, even if the underlying tech differs slightly.
Create a simple flowchart to guide teams on choosing the right hosting model (VM, K8s, Serverless, PaaS) based on factors like statefulness, traffic patterns, dependencies, operational capacity, and portability needs. Don't default to K8s for everything.
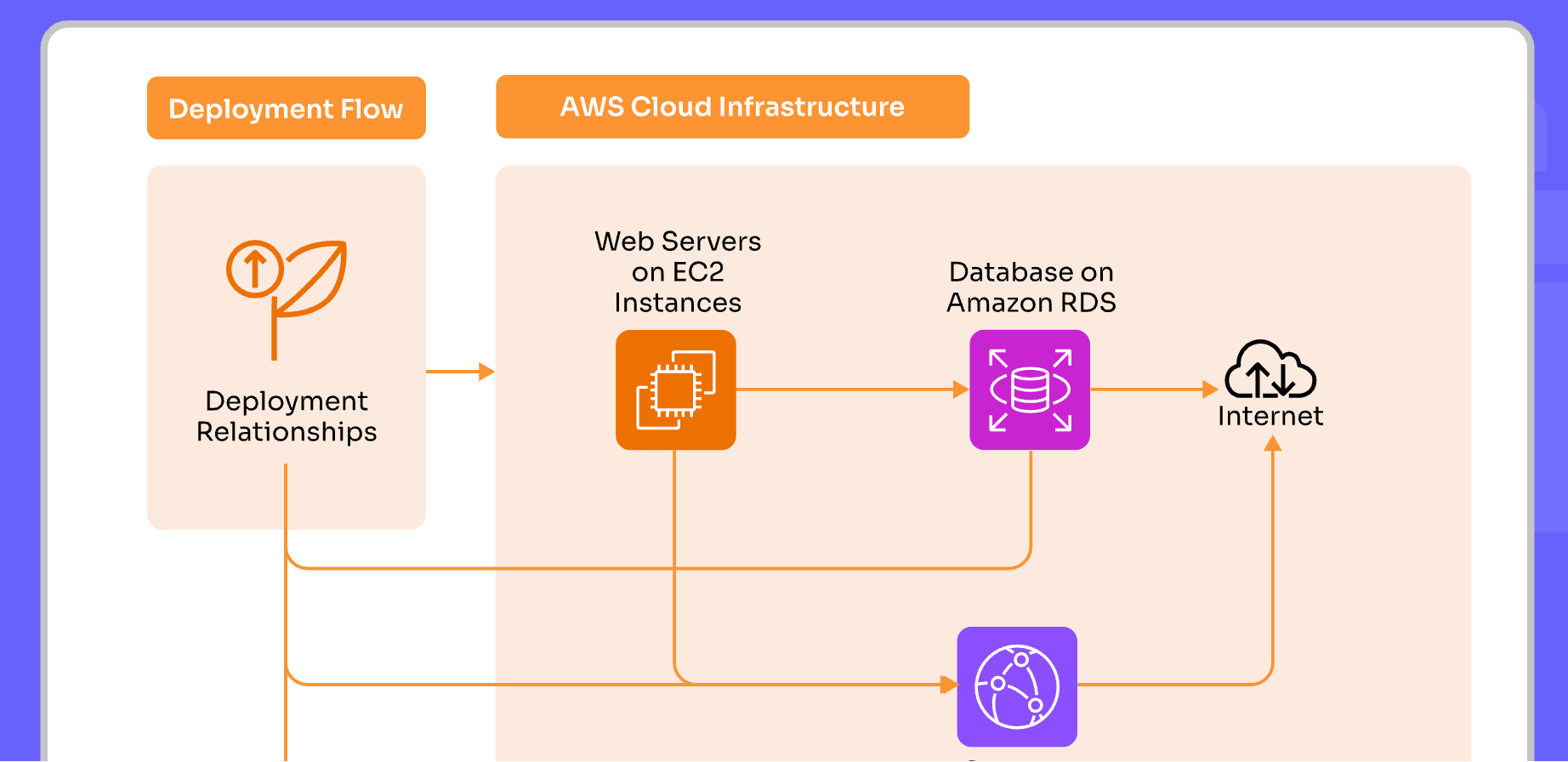
Orchestration Approaches in Hybrid
| Feature | Self-Managed K8s (Hybrid) | Managed K8s (Cloud-Specific) | Hybrid Serverless/PaaS |
|---|---|---|---|
| Control | High | Medium | Low (Platform-Managed) |
| Operational Cost | High | Medium | Low |
| Portability | High (if disciplined) | Medium (potential lock-in) | Medium (depends on platform) |
| Complexity | Very High | High | Low-Medium |
| Best For | Complex apps, full control | Faster adoption, less ops | Event-driven, simple apps |
Managing the Hybrid Beast: Operations and Optimization
Deployment is just the beginning. How do you monitor, secure, and optimize this distributed system day-to-day? Unified tooling and processes are essential. Fragmented operations lead to blind spots and inefficiency.

Unified Monitoring and Logging
You can't manage what you can't see. Siloed monitoring tools for on-premise and public cloud environments are a recipe for disaster. When things break, you need a single pane of glass.
The Blame Game: We mediated a multi-day outage for a logistics company where the on-premise team blamed the public cloud network, and the cloud team blamed the on-premise firewall. Why? They lacked unified logging and tracing. Neither team had the full picture. Implementing a centralized logging platform (like an ELK stack or Datadog/Splunk configured for hybrid) with distributed tracing was the crucial fix. Industry data suggests Mean Time to Resolution (MTTR) increases significantly in hybrid environments without unified observability.

Cost of Fragmentation: Maintaining multiple monitoring systems isn't just inefficient; it's expensive. Licensing costs, training, context-switching for engineers – it all adds up. A fintech client calculated they were spending 30% more on monitoring tools than necessary before consolidating onto a hybrid-aware platform.
Ensure application logs and traces carry unique correlation IDs that persist across service calls, regardless of whether they traverse private or public cloud boundaries. This is fundamental for effective troubleshooting in a distributed system.
Cost Management: The Hybrid Tax
Hybrid cloud can save money. It can also hemorrhage cash if not managed carefully. Egress fees, underutilized resources on both sides, licensing complexities – the pitfalls are numerous.

Zombie Resources: We frequently find orphaned VMs, unattached storage volumes, and idle load balancers racking up charges in both public and private cloud segments during our 1985 audits. One client discovered they were paying for a fleet of high-spec VMs in the public cloud that hadn't served traffic in months, alongside underutilized hardware in their own data center. Aggressive tagging, automation for resource cleanup, and regular cost reviews are non-negotiable. Flexera's 2024 State of the Cloud report (based on pre-2025 knowledge trends) highlights wasted cloud spend as a persistent, major issue.
The Egress Fee Surprise: As mentioned earlier, data transfer costs out of the public cloud can be brutal. Architecting applications to minimize egress – perhaps by keeping chatty components within the same cloud boundary or using caching strategically – is vital. A gaming company we advised shifted their analytics processing closer to their user data lake specifically to mitigate crippling egress charges.
Implement or build a dashboard that aggregates costs from all your environments (public cloud bills, private cloud amortization/operational costs). Tag resources meticulously by project, team, or application. Make costs visible and hold teams accountable.
The 1985 Approach
We don't believe in hybrid cloud for hybrid's sake. We believe in using the right resources for the right job, orchestrated intelligently. Our approach, honed across dozens of complex deployments:
- Assess Ruthlessly: Deep dive into workloads, dependencies, data gravity, and compliance needs. No assumptions.
- Strategize Deliberately: Design the target state architecture before moving anything. Focus on unified management planes.
- Orchestrate Consistently: Leverage K8s where it makes sense, but embrace serverless/PaaS for efficiency. Prioritize consistent developer workflows.
- Manage Holistically: Implement unified monitoring, security, and cost management from day one. Automate relentlessly.
- Optimize Continuously: Hybrid isn't static. Regularly review performance, costs, and workload placement. Iterate.
We’ve seen companies stumble because their partners treated hybrid as just another infrastructure project. It’s fundamentally an architectural and operational challenge. One client, a scale-up in the renewable energy sector, came to us after their initial hybrid attempt failed. Their previous partner focused only on network connectivity, ignoring orchestration and management. The result? Deployment chaos and zero portability. We helped them rebuild using a pragmatic K8s strategy coupled with unified observability, unlocking the agility they initially sought.
Is Your Hybrid Strategy Built to Last?
Hybrid cloud offers immense potential. But potential doesn't pay the bills or ship features faster. Execution does. A successful hybrid strategy requires more than just connecting networks. It demands a unified approach to orchestration, management, security, and cost control. It requires acknowledging the complexity, not glossing over it.
Ask yourself:
- Is your workload placement driven by data and dependencies, or just convenience?
- Is your security posture truly unified, or dangerously fragmented?
- Can you deploy and manage applications consistently across environments?
- Do you have real visibility into performance and cost across your entire hybrid estate?
If the answers aren't a confident "yes," your hybrid journey might be heading towards a dead end. If your current dev partner can’t map these risks and provide a clear, actionable roadmap focusing on unified orchestration and management, ping us at 1985. We build bridges, not just connect clouds.



